
What is Crypto Security? – A Complete Guide
Cryptocurrencies, or “cryptos,” are gaining widespread acceptance and seem like they’re here to stay as a long-term currency option.
Although we won’t see a global shift to cryptos overnight, it’s widely believed that it’s just a matter of time – not “if,” but “when.”
Before cryptos become the norm, there’ll be some market adjustments and changes we need to navigate.
Once viewed with skepticism, cryptocurrencies have now taken center stage in discussions about innovation and technological advancements in finance.
Whenever we talk about innovation, you can’t miss talking about cryptocurrencies.
We started with just a few cryptocurrencies, and now we have over 7,500 in the market.
Remember 2021? Cryptocurrency investments were on fire! Bitcoin up by over 60%, Ethereum more than 400%, and some small ones went up by thousands.
Thinking of jumping into the crypto game? Totally get it.
But, with great popularity comes great responsibility – this surge in popularity has also attracted some unwanted attention, with cybercriminals looking for ways to exploit vulnerabilities in your crypto assets.
Now, with the total value of assets on the blockchain surpassing $1 trillion in 2023, staying ahead of cyber threats specific to the cryptocurrency is more important than ever.
Good news, though – recent reports on crypto crime showed a promising 65% drop in illicit transaction volume by mid-2023.
However, cybercriminals are getting smarter as the blockchain world matures.
The buzz around cryptocurrencies has some downsides, especially regarding security concerns – leading to phishing and identity theft attacks.
That’s why it’s crucial to understand and tackle these security issues head-on.
Digital safety and security are real concerns – protecting yourself from hackers, ensuring privacy, and keeping exposure low.
With digital currencies like Bitcoin and Ethereum on the rise, securing your assets is super important.
This guide has your back, covering everything from picking a safe exchange to storing your crypto and spotting scams – all you need for top-notch crypto security.
What is Cryptocurrency Security?
Cryptocurrency security means keeping digital assets like Bitcoin, Ethereum, XRP, and others safe from hackers.
It uses secret codes and special ledgers called blockchains to make sure transactions are safe.
This special coding makes it really hard for anyone to spend the same money twice or make fake copies of it.
Crypto security is all about protecting these digital assets using different methods.
This keeps your money and personal info safe from cyber threats.
The reason why crypto security is so important is because of how the technology works.
The secret codes in crypto keep your digital money safe from bad guys.
These codes are like secret shields that protect every part of a crypto transaction.
They make sure that only the right person can use their coins.
So, no one else can sneak in and steal or mess with the details of the trade.
For example, Bitcoin uses these secret codes to keep every move you make with your coins secure.
This way, cryptography helps keep our online exchanges fair and safe from thieves and cheaters.
How is Cryptocurrency Secure?
In centralized networks, a security flaw can let attackers into a user’s account. But it’s almost impossible for them to hack a decentralized crypto network because they can’t steal without the user’s private key.
Here’s why breaching cryptocurrency cybersecurity is tough:
Balance
Cryptocurrency networks have many nodes with copies of the database. If an attacker changes the balance on one node, it won’t match the others. This mismatch gets rejected, creating an irregularity.
Signatures
Every transaction needs a valid signature. If one node approves it but lacks a signature, others reject it as invalid.
Protection
Crypto security blocks double-spend attacks. These attacks try to manipulate a node to show a longer transaction history, but it’s expensive and doesn’t offer enough returns.
Here are some security tips you must maintain while using crypto:
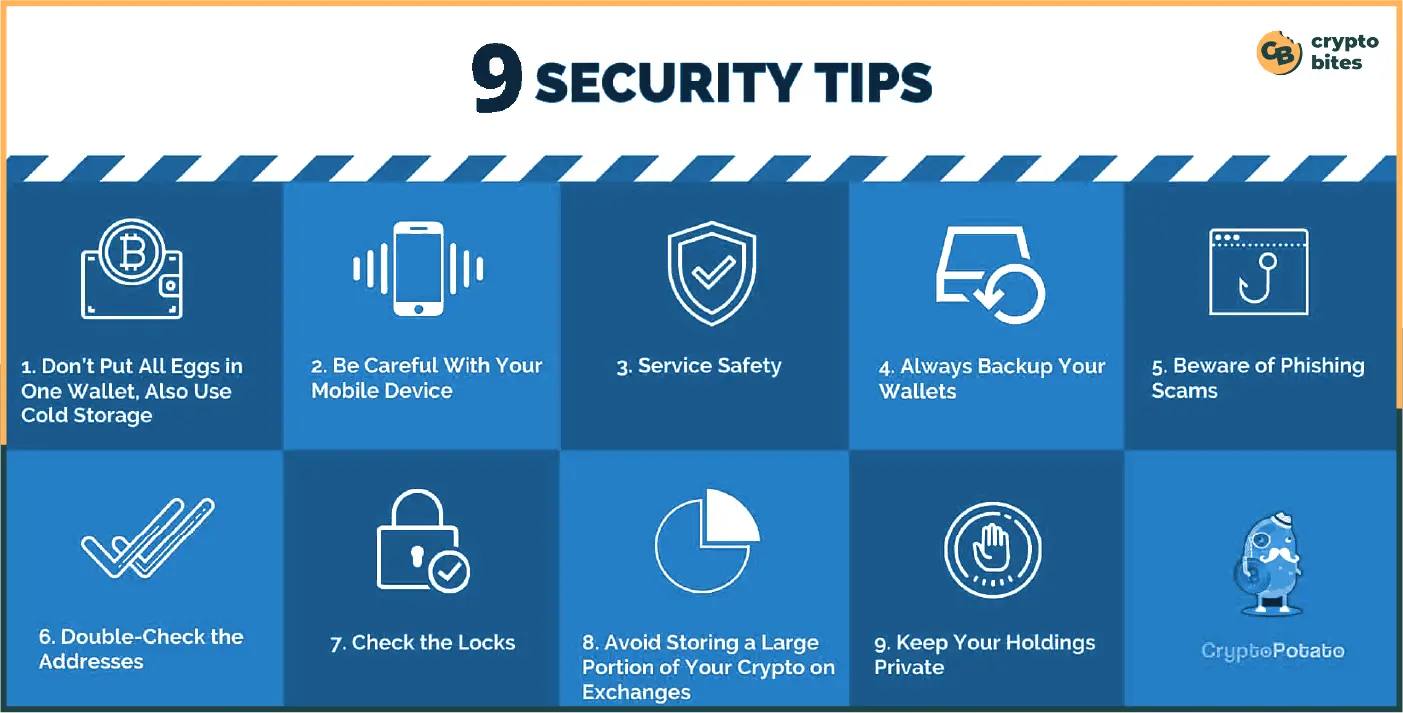
What is the Cryptocurrency Security Standard?
In 2014, a security standard called CCSS (Cryptocurrency Security Standard) was introduced in the crypto world.
The main goal of CCSS is to provide specific guidance on how to securely manage cryptocurrencies.
This standard is widely used for any information system that deals with and manages crypto wallets as part of its operations.
It’s open and concentrates on how organizations store and use cryptocurrencies.
It’s meant to enhance regular information security practices and work alongside existing standards like ISO 27001 and PCI, rather than replace them.
Unlike PCI DSS (Payment Card Industry Data Security Standard), CCSS doesn’t cover the entire transaction process but concentrates on the secure management of crypto wallets. CCSS is just about keeping crypto wallets safe.
Extra security steps are needed to protect the systems managing crypto security tools.
CCSS has three levels:
Level I ensures strong security for protecting crypto wallets.
Level II of CCSS has formalized policies and procedures, enhancing security at every step in business processes.
At Level III, critical actions involve multiple actors, advanced authentication methods ensure data authenticity, and assets are distributed across different locations and organizations.
These levels make crypto wallets tougher to hack.
CCSS is maintained by the CCSS Steering Committee, ensuring it stays neutral and up-to-date with industry best practices.
Cryptocurrency Security Standards (CCSS) outline ten steps crucial for setting up secure cryptocurrency systems.
This security system has ten steps grouped into three levels.
Most cryptocurrency exchanges adhere to this standard.
Here are the steps that many blockchain companies and organizations follow. Investors should consider companies complying with these Cryptocurrency Security Standards:
- Key/Seed Generation: Generating the essential cryptographic keys or seeds.
- Wallet Creation: Creating secure wallets for holding cryptocurrencies.
- Key Storage: Safely storing the cryptographic keys.
- Key Usage: Properly using the cryptographic keys for transactions.
- Key Compromise Policy: Establishing a policy for handling compromised keys.
- Keyholder Grant/Revoke Policy and Procedures: Outlining policies and procedures for granting or revoking access to keys.
- Third-Party Audits: Engaging in external audits by third-party entities.
- Data Sanitization Policy: Having a policy for securely cleaning sensitive data.
- Proof of Reserve: Providing evidence of the reserves held.
- Log Audits: Regularly reviewing and auditing transaction logs.
Role of CCSS and C4 in Crypto Security
There’s another group called the Cryptocurrency Certification Consortium (C4), alongside the committee we talked about.
C4 makes rules for cryptocurrencies to balance openness, privacy, security, and how easy they are to use.
They also give out certifications, so professionals can show they know about cryptocurrencies, just like they do for other skills.
Before C4, companies couldn’t really check if someone knew about Bitcoin when hiring, unlike other skills such as networking or security.
They’re thinking about creating a broader cryptocurrency certification and maybe one for checking if folks follow the CCSS rules.
Even though CCSS has been around since 2014, and there are more crypto systems now, not many groups claim they’re sticking to CCSS for handling crypto wallets.
Especially startups – many of them don’t follow good security practices, and their operations don’t meet basic security standards.
Startups often don’t spend enough time and resources on security. They don’t have strict security rules in place, and they don’t test their systems regularly.
All these things make startups more attractive but also more likely to get hit by cyber breaches.
Looking at recent breaches, every system hit by a big crypto attack wasn’t following CCSS Level 1.
But those meeting CCSS Level 2 or higher have a better chance against cyber attacks targeting how cryptocurrencies work.
For IT audits, checking CCSS compliance is a good way to make sure the risks of managing crypto wallets are being handled.
Key Elements of Crypto Security
It’s crucial to keep your cryptocurrency safe, and that starts with understanding the key elements of crypto security. Here are some of those elements.
Private and Public Keys
Cryptocurrency users each have unique cryptographic keys.
The public key is like an address that others can see and use to send funds, while the private key must be kept secret to control spending.
Cold and Hot Wallets
A cold wallet is a cryptocurrency wallet not connected to the internet, such as a hardware or paper wallet.
It’s safer from online hacks.
On the other hand, a hot wallet is connected to the internet, making it more vulnerable but convenient for regular transactions.
Two-Factor Authentication (2FA)
Adding an extra layer of security, 2FA requires users to provide two types of identification before accessing their crypto assets.
Regular Updates
Keeping software up-to-date ensures that potential vulnerabilities are fixed, reducing the risk of a security breach.
How to Choose a Secure Crypto Exchange?
When picking an exchange, consider its security.
In 2021, Bitmart lost over $200 million in a hack, and Crypto.com lost $35 million.
Both promised to repay affected users.
Other big exchanges like Binance, Bitfinex, KuCoin, and more have faced hacks, but they also reimbursed users.
To avoid risks, check how much of an exchange’s crypto is in “hot wallets” online.
The safest exchanges keep only a small amount online and store the rest offline to minimize losses in a major hack.
Use exchanges that reimburse users for hacks, and the better ones have a reserve fund for this.
If an exchange got hacked before and didn’t repay users, it’s a red flag to stay away.
How to Keep Your Crypto Investments Secure?
Before getting into crypto, it’s crucial to know it isn’t insured by the FDIC.
If an exchange goes bankrupt or a hacker steals your crypto, you might lose everything, and recovering stolen or lost crypto is often impossible.
The good news is that there have been significant improvements in crypto safety.
To safeguard your crypto investments, consider these steps:
Active Trading
Only leave your cryptocurrency on an exchange if you’re actively trading. Otherwise, move it to an external wallet.
Exchange Security
Ensure your exchange is secure, use two-factor authentication for added protection.
Wallet Security
Secure your wallet by encrypting your keystroke file, keeping a paper backup of your seed words, and using a cold wallet when possible.
Choose a Secure Wallet
Ensure you use secure wallets known for strong security features. Hardware wallets, keeping private keys offline, offer higher security than online ones.
Enable 2FA
Implement Two-Factor Authentication (2FA) for added security. 2FA means even if your password is hacked, attackers still need the second factor to access your account.
Keep Everything Updated
Ensure your devices, wallets, and apps are always up-to-date. Updates often include security improvements against new threats.
Use Safe Networks
Avoid making crypto transactions over public Wi-Fi networks. These networks might be insecure, allowing hackers to grab sensitive data. If you must use public Wi-Fi, use a virtual private network (VPN) for safety.
Watch Out for Phishing
Stay alert for phishing attempts, especially in crypto-related emails. Always double-check emails asking for sensitive info or directing to unfamiliar sites. Avoid using fake software or websites and never enter your seed words anywhere online.
Crypto Security Using 2FA
Choosing a trustworthy exchange helps guard against their mistakes causing problems.
But if your account is hacked, and it’s not the exchange’s fault, you might not get your money back.
That’s why turning on 2FA is crucial.
With 2FA, you need to enter a code from a text or app every login or withdrawal, adding a layer of security.
It prevents crypto theft even if your email is compromised.
Without 2FA, if someone gets into your email, they can change your password, locking you out and transferring your crypto without your say.
Exchanges usually won’t refund you if this happens.
Avoid using text messages for 2FA, as attackers can intercept codes using SIM hijacking.
Using a mobile app like Google Authenticator for 2FA is a safer choice.
Common Risks in Crypto Security
Even if your crypto is in a super secure wallet, you can still get caught by common crypto scams if you’re not familiar with them.
So, let’s talk about what to watch out for.
Phishing Scams
There are many fake websites pretending to be real ones, asking for your wallet’s seed words.
These deceitful websites are called “phishing sites,” a common scam in crypto.
For instance, you might think you’re on the real Uniswap site at app.uniswap.org, but you’ve actually landed on app.uniswop.org (note the different spelling!).
Hackers create sites that look identical to the official ones but with a slightly changed URL to trick users.
Avoiding these scams is pretty straightforward, though.
Never enter your seed words or private key on any website.
Even if a page seems like your wallet asking for seed words while you browse, don’t enter them.
Your wallet might ask for your password but never your seed words during web browsing.
Seed words are needed only during setup.
If you forget your password or can’t access your account, delete your wallet from your device.
Then reinstall it and, using a blank browser page, enter your seed words to recover your account.
Remember, this step should be done only once, right after installing.
Fake Wallets
Another common crypto scam involves fake wallets.
Scammers create software resembling popular wallets like Metamask and promote it on platforms like Google Ads or Facebook.
Clicking the ad takes you to a site where you can download what seems like a legitimate wallet.
But this altered software secretly sends your seed words to the scammer once generated.
They wait until you transfer crypto to the wallet, then swiftly move it to their own.
To stay safe, download your wallet only from the official website.
Be cautious of ads, especially since wallets usually don’t advertise.
If you search for a wallet on Google, scroll to organic results, avoiding ads.
Avoid searching within app stores; they may unintentionally feature scam wallets.
Instead, visit the wallet’s official site and use the provided link to reach the app store page.
Malware
Another common crypto scam involves infecting your computer with malware.
A scammer might email you, tricking you into downloading and running a file.
Once you run it, your computer could get secretly infected with malware that spies on your actions.
Here are some simple tips to avoid losing your crypto to malware:
Avoid using a wallet password that’s the same as other website passwords.
Never take a screenshot of your seed words.
Be cautious about downloading email attachments; verify the sender’s address before downloading any files.
If possible, use a different device for checking your inbox than the one you use for crypto.
Consider using a hardware wallet if available; they offer added security against such attacks.
Wrapping Up
Cryptocurrencies are designed to be super secure, making it nearly impossible for anyone to mess with who owns them or their transaction details.
But here’s the deal: there are still some vulnerabilities, and hackers are getting creative with new ways to attack crypto exchanges and individuals holding cryptocurrencies.
So, what’s crypto security all about? It’s like putting a digital lock on your crypto to stop unauthorized folks from getting in and swiping it.
Crypto security uses cryptography to secure transactions and relies on blockchain for transparency and decentralization.
As cryptocurrencies gain popularity, it’s crucial to prioritize security measures to protect assets and maintain trust in the digital currency world.




